Spamdexing, which is a word derived from “spam” and “indexing,” refers to the practice of search engine spamming. It is a form of SEO spamming.…
Systemd is a modern init system and service manager for Linux operating systems. systemd is the mother of all processes and it is responsible for…
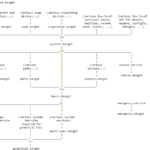
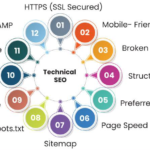
Technical SEO refers to the process of optimizing the technical aspects of a website to ensure that it meets the requirements of modern search engines…
Termux is a versatile and powerful terminal emulator and Linux environment app for Android. It allows users to run a Linux distribution alongside their Android…
A title tag is an HTML element that specifies the title of a web page. Title tags are displayed on search engine results pages (SERPs)…
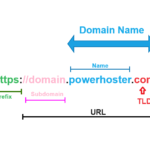
A Top-Level Domain (TLD) is the last segment of a domain name located to the right of the dot (“.”). It is the highest level…
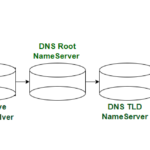
A Top-Level Domain (TLD) Nameserver, also known as a TLD Nameserver or TLD DNS server, is responsible for handling DNS queries related to a specific…
What is Two’s Complement ? One’s Complement solves the problem of signed bit operations, but there is still a problem that is not solved, that…
UNIX is a powerful, multitasking, multi-user operating system originally developed in the 1960s and 1970s at AT&T’s Bell Labs. It was designed to be a…
In SEO (Search Engine Optimization), user experience (UX) refers to the overall experience that users have when interacting with a website or webpage. It encompasses…
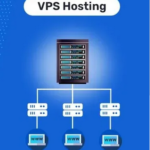
VPS hosting stands for Virtual Private Server hosting. It is a type of web hosting that provides a virtualized server environment for websites or applications.…
Vulnerability scanning is a process used to identify security weaknesses and potential vulnerabilities in computer systems, networks, applications, and devices. It involves using automated tools…